Build a More Secure Web using npm with Deno
npm has made software easily accessible and usable, growing and enriching the JavaScript community. However, since Node installs and runs dependencies by granting full access to the filesystem, environment, the internet, etc., Node programs are more susceptible to supply chain attacks.
Supply chain attacks are nothing new. But given that the npm registry is the largest in the world, with more and more JavaScript developers using it to build apps and websites, npm is a constant target for these dependency attacks.
Deno makes npm better and building with it is more secure, since Deno’s secure-by-default and unique sandboxed architecture help mitigates dependency based attacks.
Secure by default
Malicious npm modules have been reported to steal user data from forms, perform shell injection attacks, and install malware onto your machine. These attacks are more likely in Node because Node apps (and its dependencies) all have unfettered access to everything—the filesystem, the internet, environment variables, etc.
Below is a demo of a particularly sinister shell injection attack using bin script confusion:
Deno runs code in a sandbox and uses an “opt-in” permission model. That means unless you specifically enable it, a program run with Deno has no file, network, or environment access. Access requires permissions granted through command line flags or a runtime permission prompt:
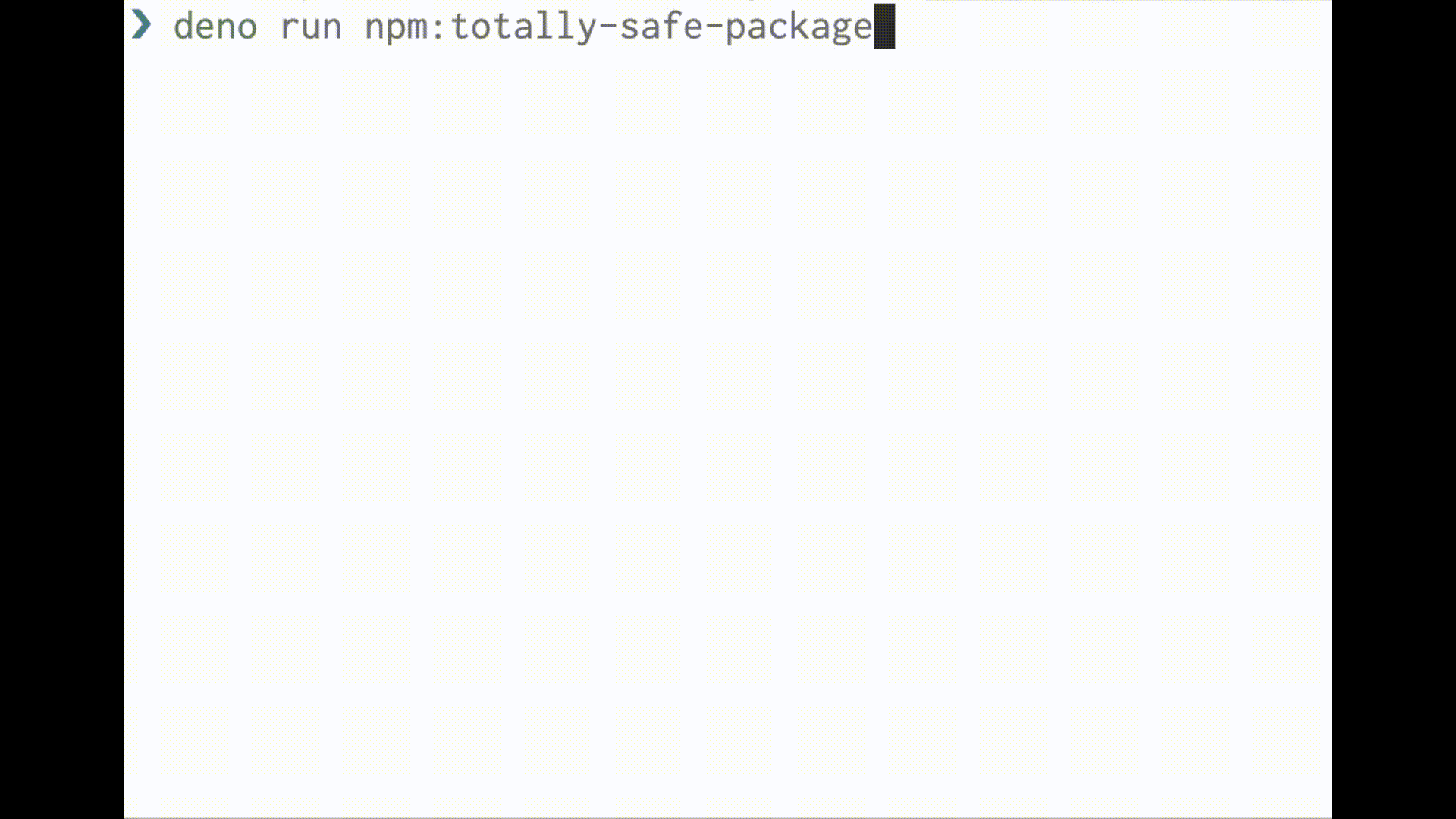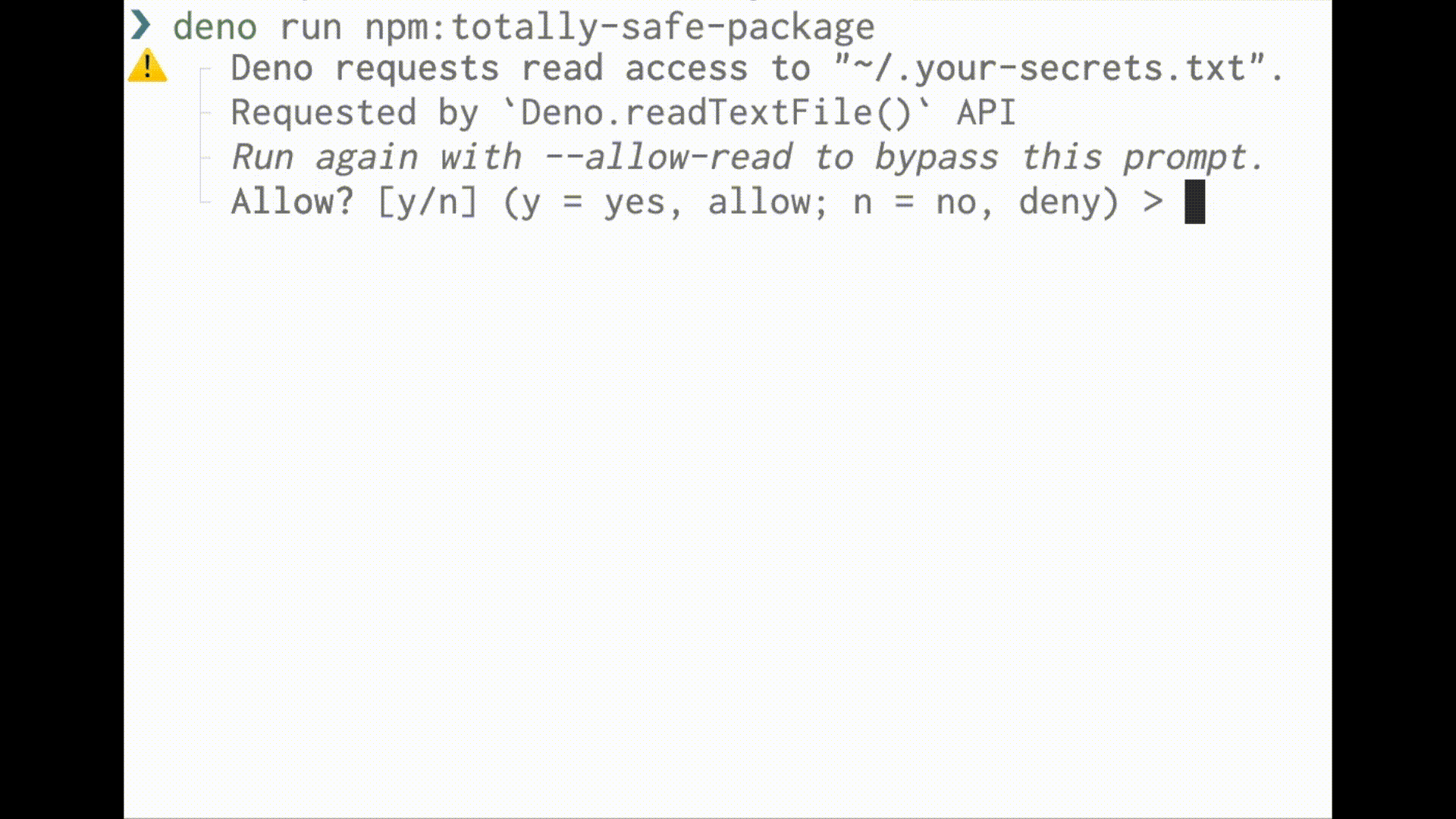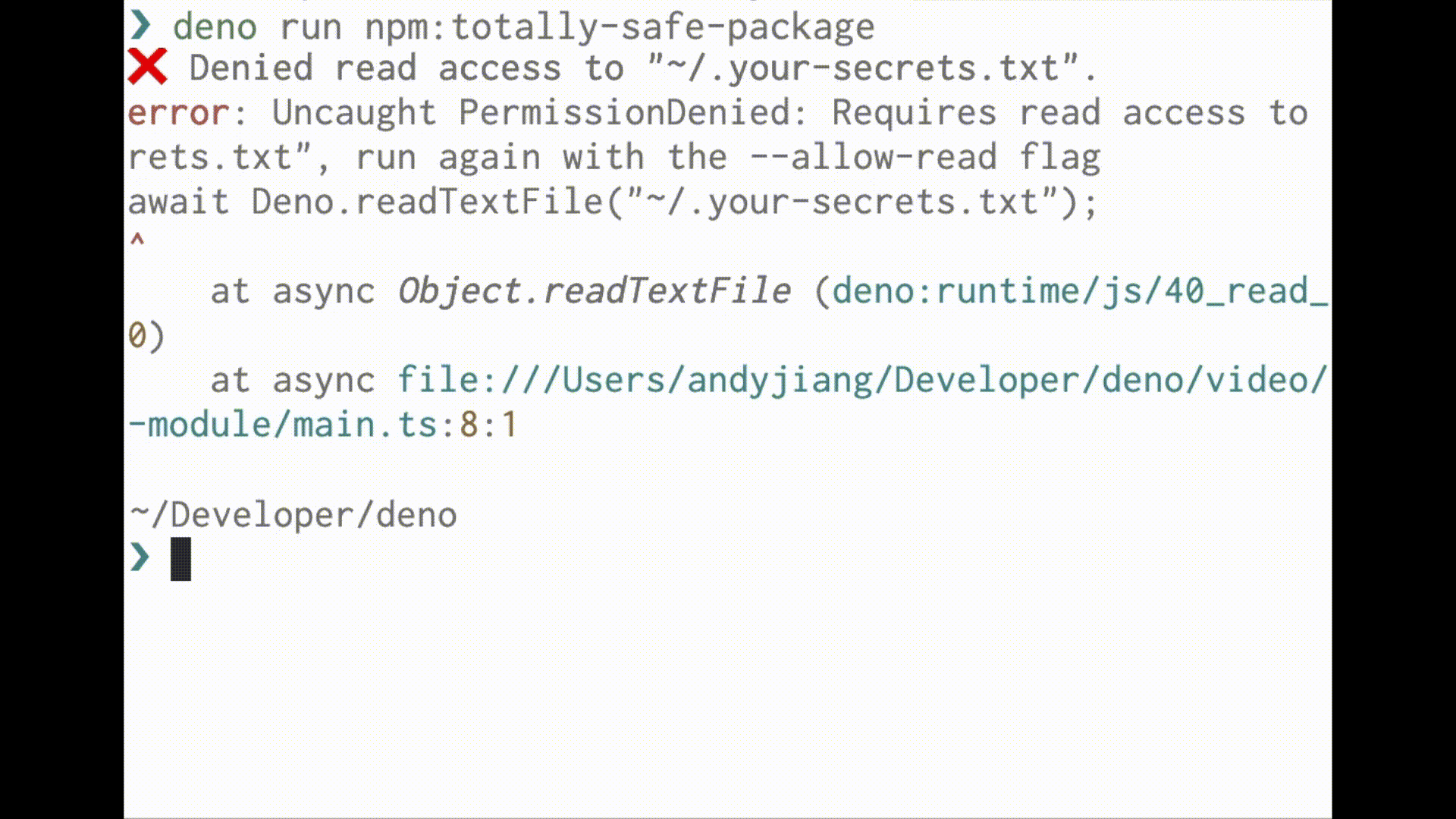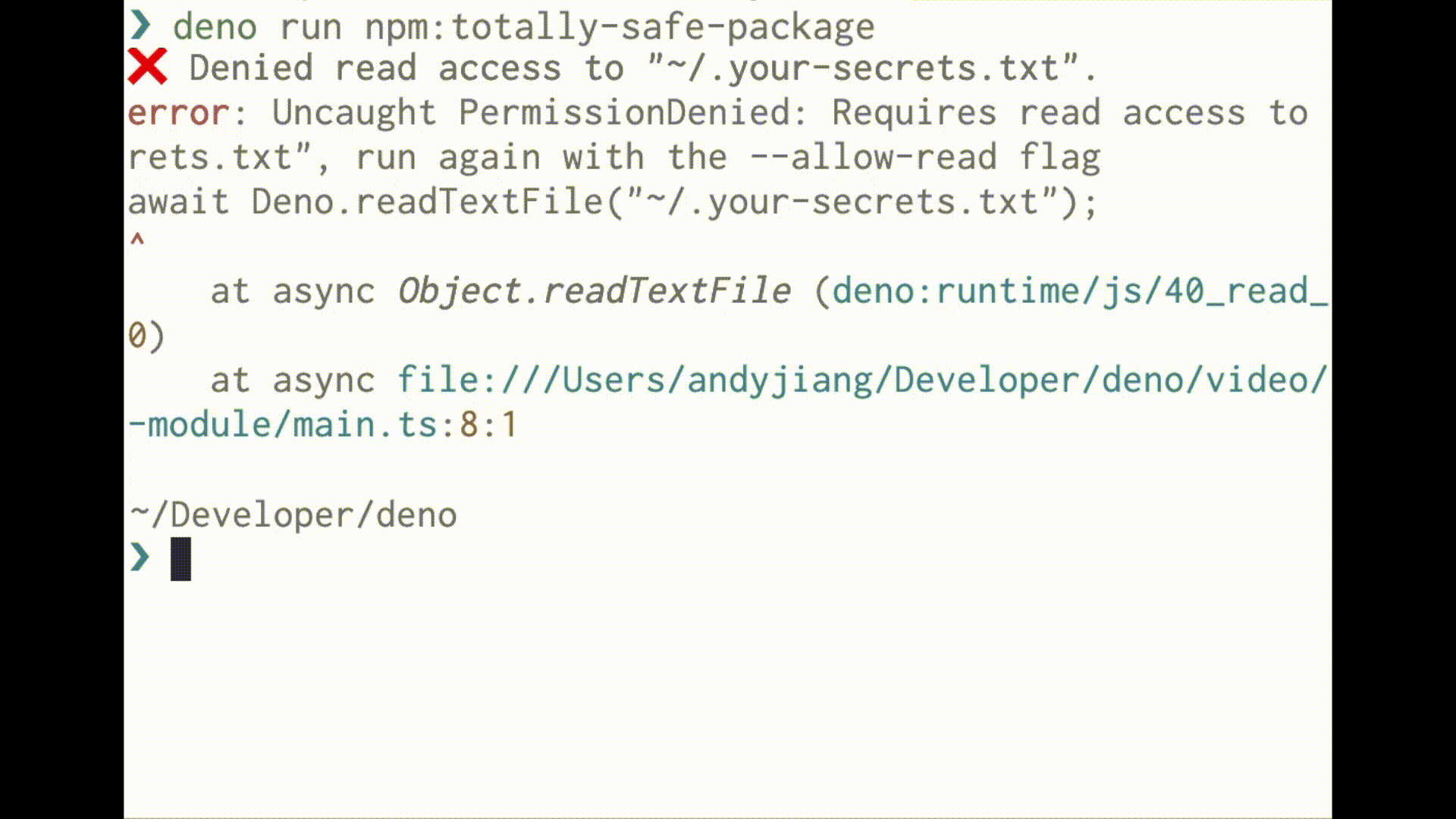
For a full list of permissions, see here.
When you run a script with Deno, you are aware of what access it needs.
Sandboxed Architecture
Deno’s permission model succeeds since the program is executed in a sandbox, which has a narrow entrypoint with few APIs to external systems. This makes it easy to manage all the data going to and from the code.
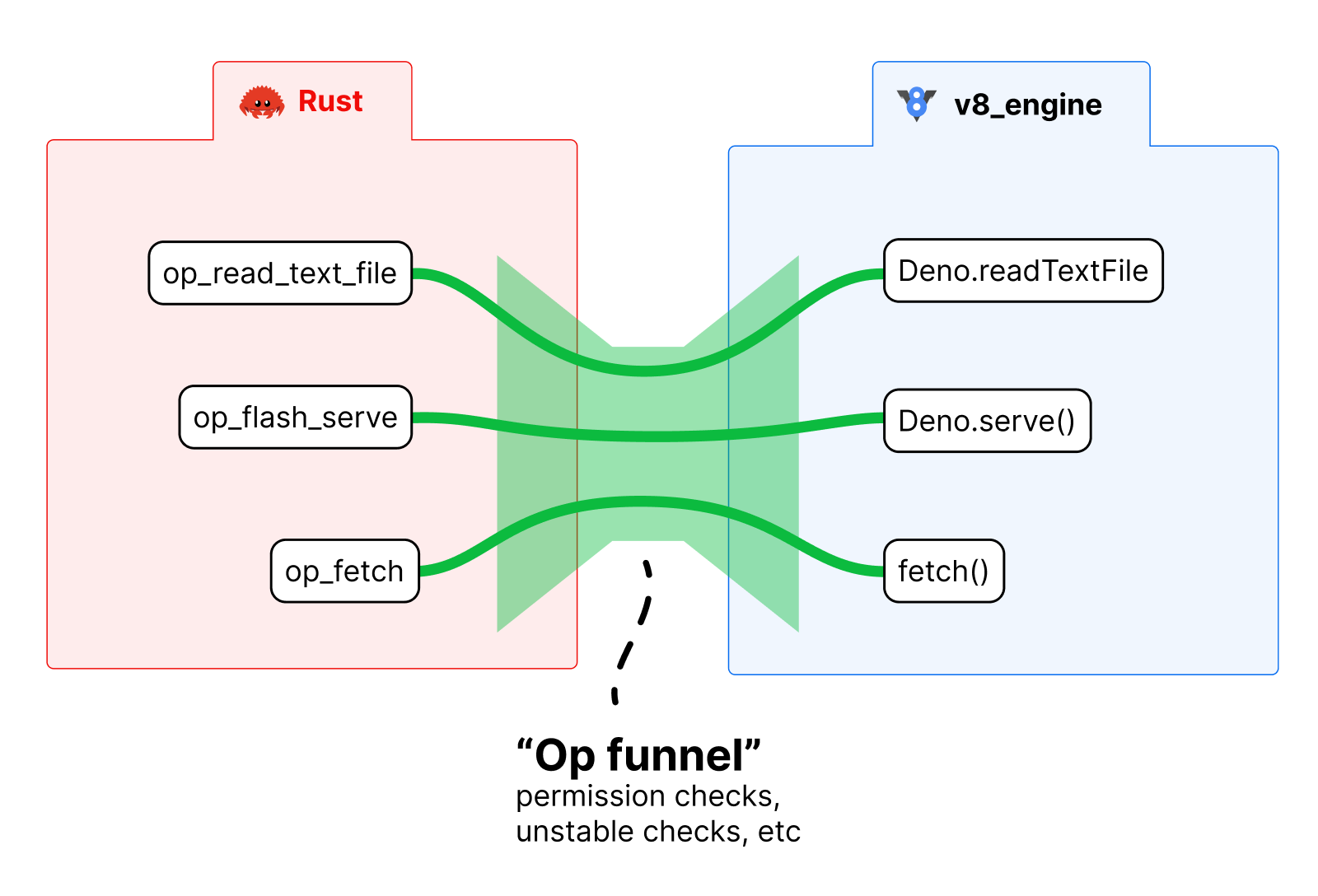
Like a Browser
Deno’s security system is borrowed from the privacy model of modern browsers.
Whenever your browser requires access to your webcam, microphone, even geolocation API, it prompts you for permission. This means (theoretically) you are fully aware of the access the website you’re visiting has of your computer.
Deno is similar, in that it puts the control in your hands. When executing third party, untrusted code, or a random dependency, you are aware of what it needs access to.
What’s next?
Being able to browse the web safely is critical to its growth and usage. Building a more secure web with npm is easier with Deno, with its sandboxed, opt-in permissions approach helping to mitigate supply chain attacks.
What are you building with Deno? Let us know on Twitter or Discord!
